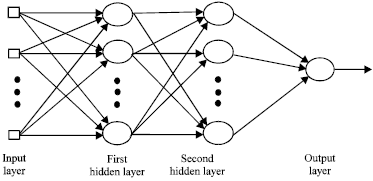
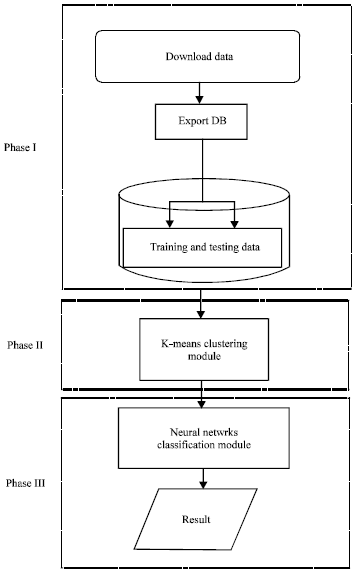
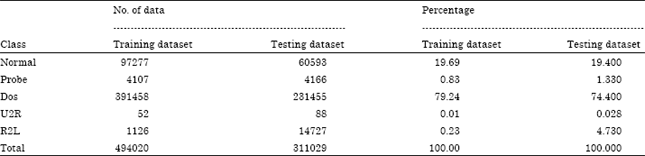
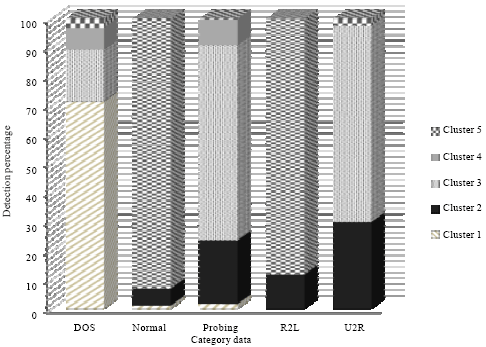
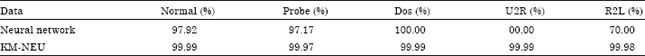
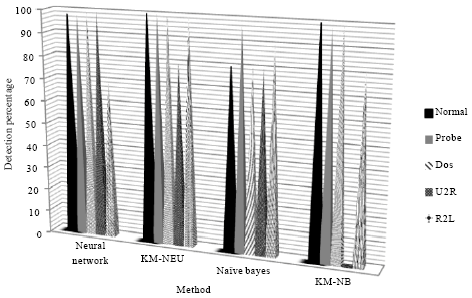
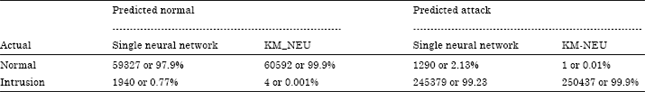
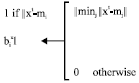Research Article
KM-NEU: An Efficient Hybrid Approach for Intrusion Detection System
Faculty of Computer Science and Information Technology, University Putra Malaysia, UPM Serdang, 43400, Selangor, Darul Ehsan, Malaysia
Zaiton Muda
Faculty of Computer Science and Information Technology, University Putra Malaysia, UPM Serdang, 43400, Selangor, Darul Ehsan, Malaysia
Warusia Yassin
Faculty of Information and Communication Technology, University Technical Malaysia Melaka, Durian Tunggal, 76100, Melaka, Malaysia
Nur Izura Udzir
Faculty of Computer Science and Information Technology, University Putra Malaysia, UPM Serdang, 43400, Selangor, Darul Ehsan, Malaysia